Geofence Warrants
How does a geofence warrant work?
It's just past midnight and three drive-by shooting just occurred in your city. As luck would have it, no witnesses can be found to identify the vehicle; the victims are not talking... Lacking leads, this case could be unsolvable. A geofence warrant may be the only solution.
We make writing geofence warrants as easy as Point, Click, Warrant. Warrant Builder puts decades of warrant writing and cybercrime investigation expertise at the fingertips of every officer, empowering them to tackle any investigation no matter how complicated. Warrant Builder helps law enforcement create both Advanced Location Tower Dump and Google geofence warrants with integrated mapping and return analysis tools.
A geofence warrant is a legal order obtained by law enforcement agencies to collect data from electronic devices within a specific geographical area during a particular timeframe. It allows investigators to acquire information such as GPS coordinates, timestamps, and other relevant data from mobile devices, wearables, and connected cars that may be present within the designated area.
The process begins by establishing a virtual perimeter, known as a geofence, using GPS coordinates. The warrant specifies the area and time period during which data will be collected. For Advanced Location Tower Dump, both AT&T and T-Mobile require a radius from a point; Google allows for shapes like squares and polygons. In our drive-by shooting case, a perimeter around the three victim's residence would be created. When the geofence process is complete, a phone that was found in all three locations may be identified; thats your suspect.
Looking for a Google geofence warrant primer? Check out our deep dive blog post: Writing Google Geofence Search Warrants.
Multi-phase warrant process
In order to comply with the requirements of US v. Chatrie, geofence warrants require a phased approach. By segmenting the warrant process into distinct phases, the privacy of unrelated persons can be protected.
When devices within the geofence are identified by Google, they are assigned an anonymized identifier that only temporarily specifies a single device for the period of the warrant process. AT&T and T-Mobile use IMSI numbers as their form of anonymized ID. Once the warrant phases have been completed, the anonymized identifiers are deleted by Google. It is also important to note that unlike other "anonymized data" on the internet, an "obfuscated ID" cannot be be used to identify a device or person by anyone other than Google. Similarly, only the telecoms know what IMSI number is assigned to which customer.
Phase 1
Create your initial search areas.Phase 2
See how specific devices entered or left your crime scene.Phase 3
Unmask the relevant devices with basic subscriber information.Phase 4
Collect additional account specific evidence from Google.Warrant Builder's approach
Warrant Builder guides you through each phase adding all the required language depending on where you are in your investigation. Warrant Builder is so much more than a geofence search warrant template, Warrant Builder instantly maps your warrant returns directly from your warrant; no need to external websites or software. We have simplified the geofence warrant process down to the fewest possible questions letting you focus on the probable cause while we take care of the rest.
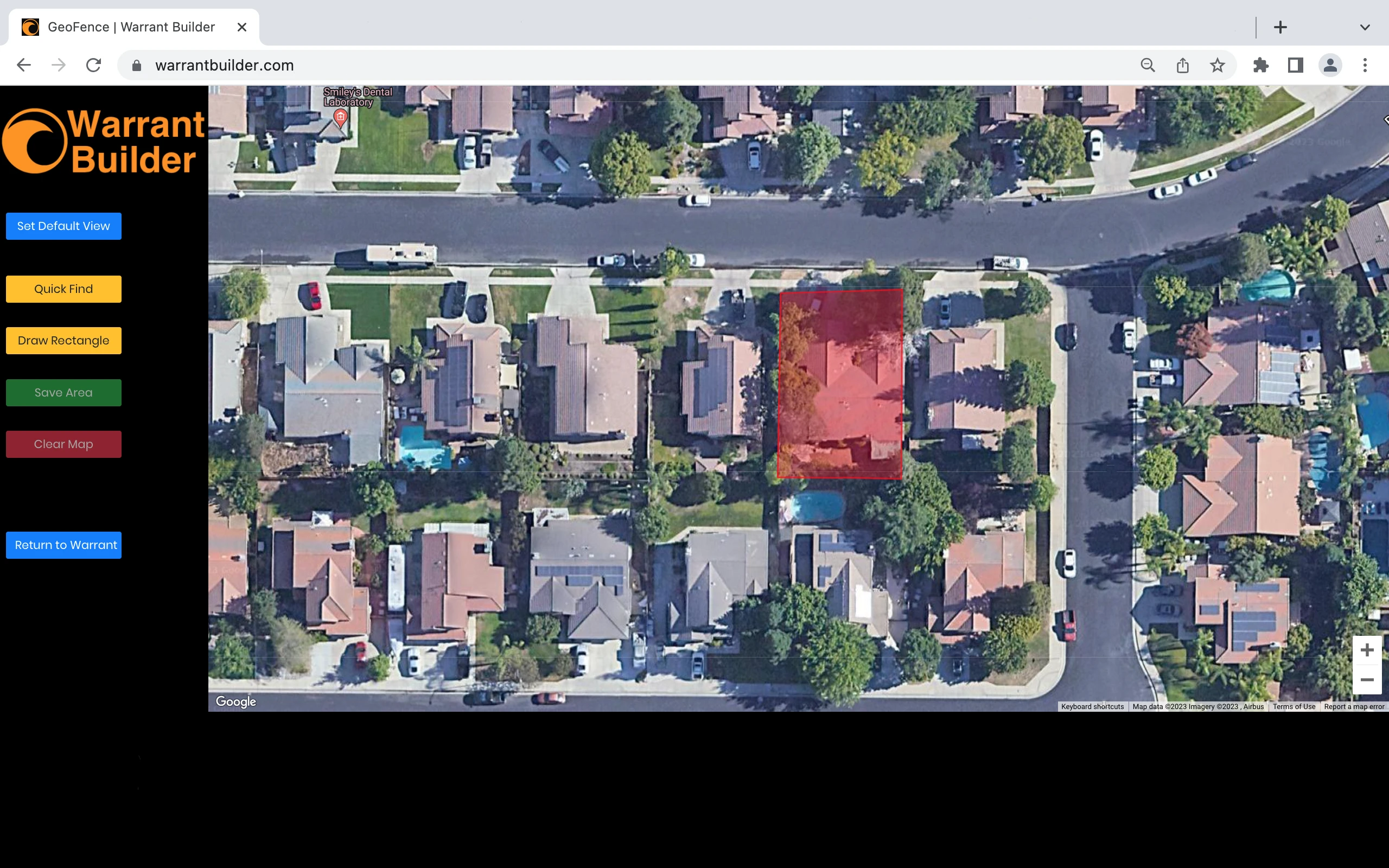
Phase 1 - Initial Search Area
The initial search area is the first phase of the warrant and identifies the location(s) to be searched. It is recommended to have more than one location if possible to look for devices that are common to both. For example, where the car was stolen and where the car was left. The narrower the window of time, the better.
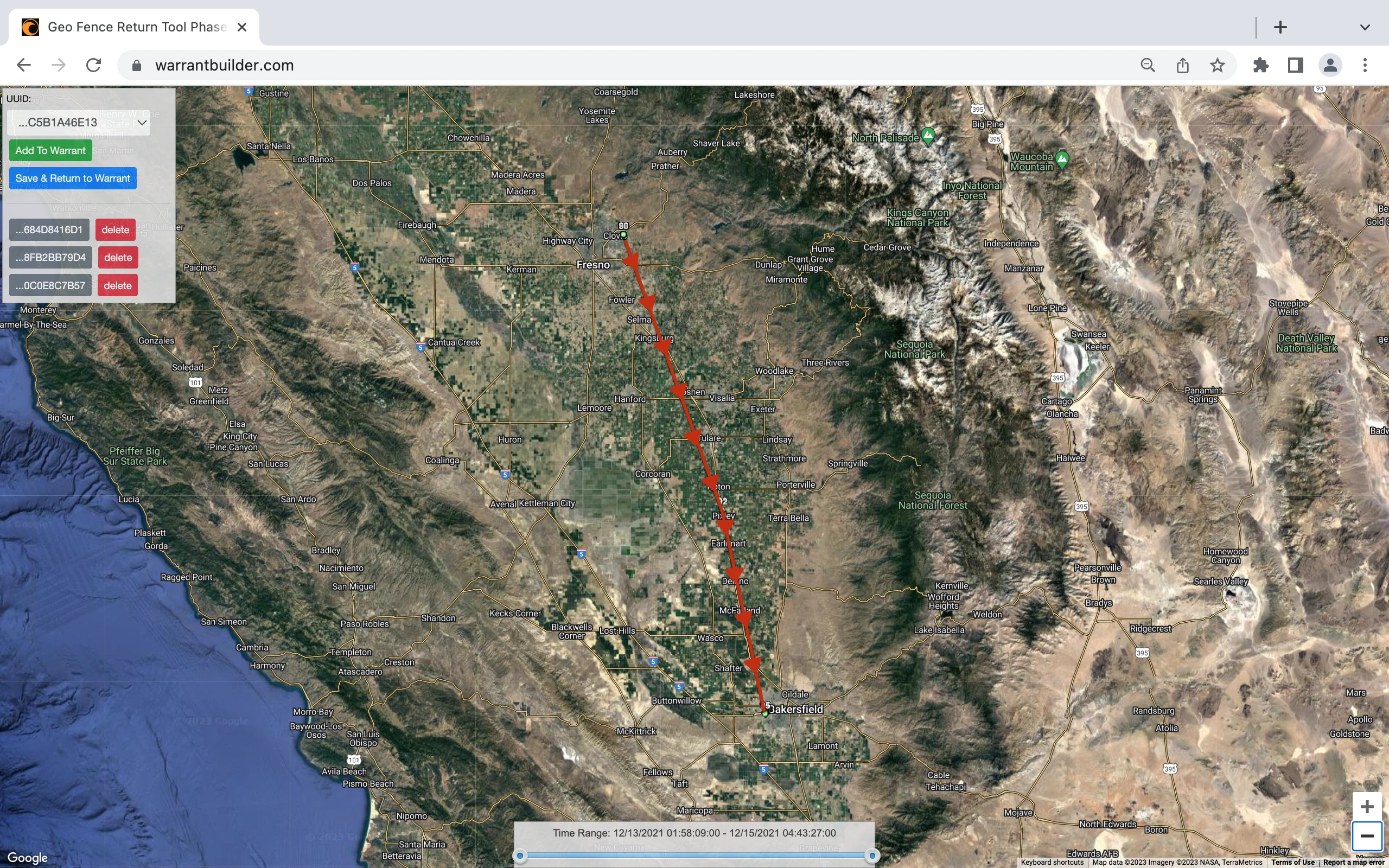
Phase 2 - Movement Information
Next comes the mapping of record returns from Google. As seen below, several devices were identified by their Anonymized IDs. These temporary numbers are assigned to represent mobile phones located within the search area.
Example Anonymized ID 010101BD55464DAC6520C124E72FF65A6E7D15F2F4E4D51F913A5DEBAFF6F3891341012D8950D7

Phase 3 - Device Unmasking
After mapping the Phase 2 record returns from Google, the investigator gets a better picture of the location activity for each specified device. The movement information may show that a device momentarily passed nearby the crime scene and continued on their way. The device may have belonged to a delivery drive showing them driving up and down the neighborhood streets stopping frequently along the way. The movement information may very well show the phone enter the crime scene and linger for an unusual amount of time. The investigator would likely discard the anonymized IDs for phones one and two, focusing their next warrant on phone three.
Phase 3 of the search warrant process requests that Google "unmask" the anonymized device(s). For those specified devices Google will provide basic subscriber information such as name, email address, and device identifier.
Benefits of Geofence Warrants
- Enhancing Investigation Efficiency: Geofence warrants can significantly expedite investigations by allowing law enforcement to focus on individuals who were present within a specific area during a particular timeframe. This targeted approach helps narrow down suspects and potentially leads to faster resolution of cases.
- Gathering Evidence: Geofencing provides investigators with access to critical device location and movement patterns. This evidence can strengthen criminal cases, verify alibis, establish connections between suspects, and unravel intricate criminal networks.
- The warrant of last resort: Geofence Warrants are primarily used when all other leads are exhausted to solve the unsolvable case. They serve as a digital witness to the crime, possibly identifying involved persons. Knowing how that phone came into a crime scene and where it traveled to after may be the break in the case that law enforcement never would have had without the geofence.
Disadvantages of Geofencing
- Privacy Concerns: One of the main concerns surrounding geofencing is the potential invasion of privacy on unrelated persons. A mobile phone located within a crime scene likely belongs to one of three categories of persons: suspects, victims or witnesses.
- False Positives: Geofence warrants are not foolproof and can generate false positives, identifying innocent individuals in criminal investigations. False positives could be due to poor location accuracy reporting by a mobile phone or the devices connection to Wi-Fi instead of mobile data GPS coordinate reporting.
Search warrants are required to be specific, and Warrant Builder's Geofence tool maps your search area coordinates within 4" of accuracy. Testify with confidence that you have defined the search area as accurately as possible. This level of accuracy will help with Judges that don't want infringement on neighbors.

