
IP addresses are at the heart of every online investigation. Knowing how to investigate IPs can take you from a Social Media account to the suspects home with a simple search warrant. In this edition of the Warrant Builder Cybercrime Field Guide we cover IP addresses and how to investigate them.
An IP address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It works like a home address for your computer or any device that connects to the Internet. Just like how your home address tells the mail carrier where to deliver your letters, an IP address tells the Internet where to send information. Every device that connects to the Internet, like your phone, tablet, or computer, gets a unique IP address so that it can send and receive information without getting mixed up with other devices. This way, when you visit a website or send an email, the information knows exactly where to go and how to get back to you.
IP Addresses are a part of using any internet connected service, from WhatsApp to Cellular Investigations.
Important Terms
- Domain: A domain is a specific area of the internet defined by a unique name, often used to identify websites.
- Domain Name: A domain name is a human-readable address used to access websites, like “WarrantBuilder.com”.
- DNS: DNS (Domain Name System) is a system that translates human-readable domain names (like example.com) into numerical IP addresses that computers use to identify each other on the internet.
- Truncated: Truncated means shortened by cutting off a part, often used in reference to abbreviating lengthy data.
- VPN: A VPN (Virtual Private Network) is a service that encrypts your internet connection to protect your privacy and secure your data.
- Canonical Name: A canonical name (CNAME) is an alias used in DNS to point one domain name to another.
- Internet of Things: The Internet of Things (IoT) refers to the network of physical devices connected to the internet, sharing data and enabling smart interactions.
IP Address Format
As you investigate online crimes, you will encounter two forms of IP addresses: IP version four (IPv4) and IP version six (IPv6). Both do the same thing with IPv6 having some technical advantages. From an investigators perspective, they serve the same function and are investigated the same way.
IPv4 Format: IPv4 addresses are 32-bit numbers, typically represented as four decimal numbers separated by dots (e.g., 44.240.245.25). IPv4 will always have four sets of numbers with a maximum value of 255 in each set.
IPv6 Format: IPv6 addresses are 128-bit numbers, represented as eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:0000:1234:0000:0567:0008:0001).
Why have two different types of addresses? Basically, we ran out and had to come up with a solution to create more. IPv4 can support approximately 4.3 billion unique addresses which, in the early days of the internet, was plenty. Now millions of devices require internet connectivity and generally speaking each IP needs to be assigned to a unique device. When Internet of Things (IOT) devices like a smart toaster need to connect to the internet, you can see how we can run out. IPv6 can support an almost limitless number of unique addresses, solving the exhaustion problem faced by IPv4.
IP Address Lookups
To determine who an IP address is assigned at the time of the crime, a search warrant is required; but how do you know what company to send the warrant to? A WHOIS lookup will tell you what company owns your suspect’s IP address.
There are many publicly available WHOIS websites, but I suggest using the American Registry of Internet Numbers, https://search.arin.net, for official documentation in an investigation. ARIN is one of the five regional Internet registries (RIRs) that manage the allocation and registration of Internet number resources and is the authority for North America.
While it is best practice to use ARIN, my favorite is https://centralops.net/ because third-party WHOIS websites pull their information from ARIN and are usually easier to read.
For the example below we will be using the IP address of WarrantBuilder.com which is 44.240.245.25, an IPv4 address. The screenshots below are from CentralOps. To begin, simply type or paste in the IP address you want to search and click the Go button.
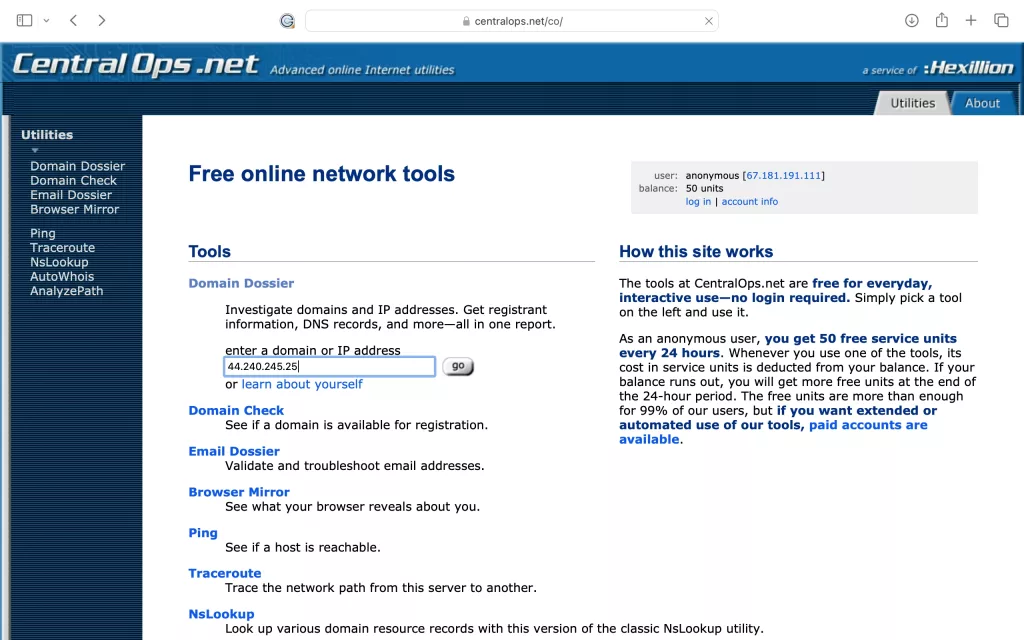
Lets review our results!
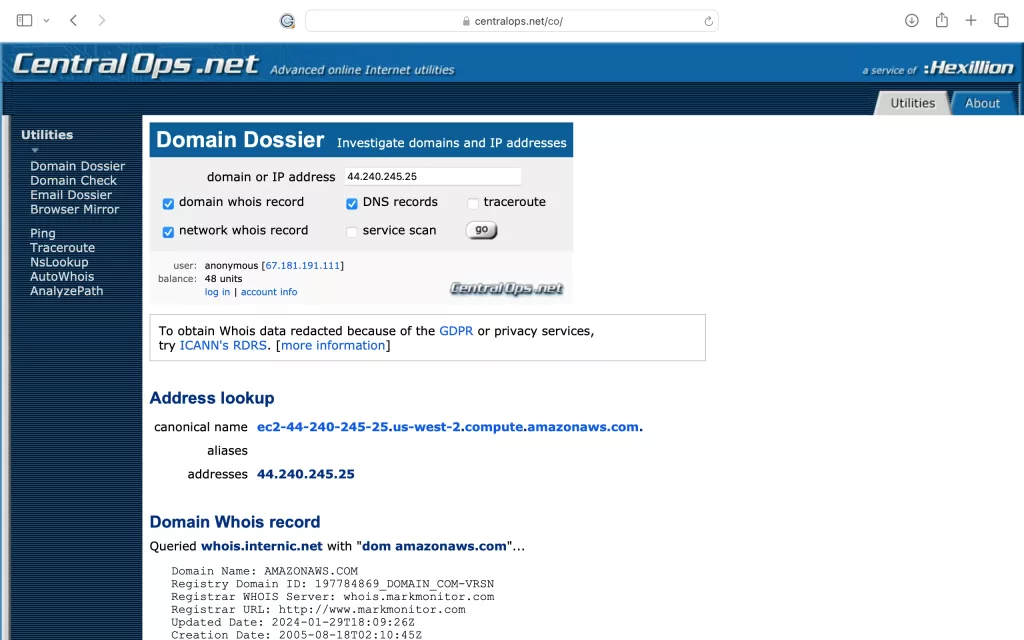
The first field in the results under the Address lookup heading is the canonical name; most of the time this will be blank. It is showing up in our example because the Warrant Builder website is hosted at the IP address we searched.
The Domain Whois record section is where the information we care about is listed. The Domain Name: field identifies the company who owns the IP address. In this example it says AMAZONAWS.COM because the IP Address is owned by Amazon. Normally you will see a common ISP like Comcast, AT&T, T-Mobile, etc. Whatever company is listed in the Domain Name field is where you will address your search warrant. They can provide the subscriber information of who was assigned the specific IP address at the time of your crime.
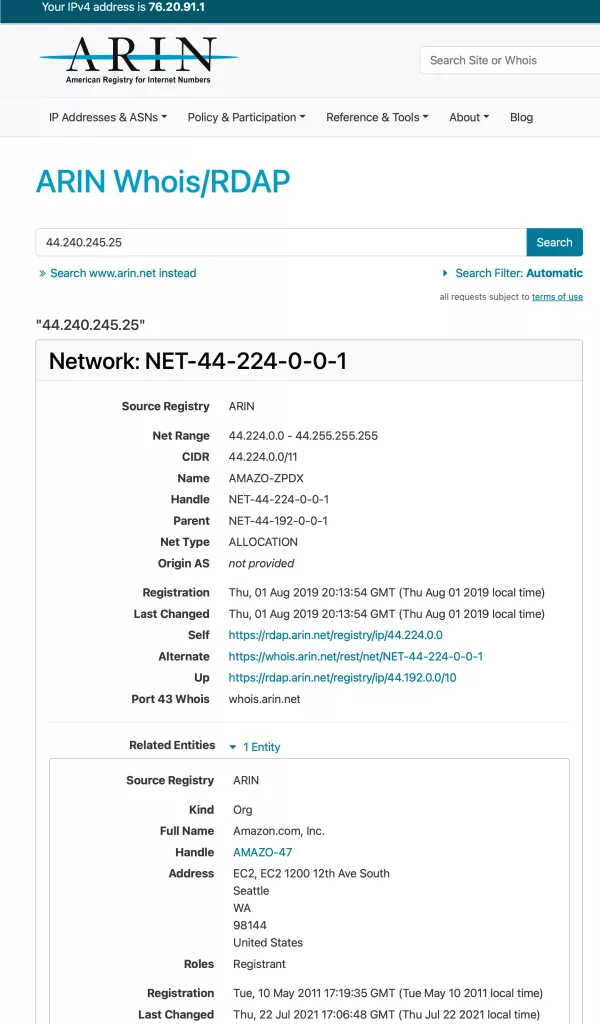
For comparison, the screenshot below is the same result from ARIN. As you can see, it is much long and harder to read.
IP Address Geolocation
The second most common question asked by Investigators is where the IP address is physically located. There are many IP Address Geolocation websites, and the underlying technology is rather complicated. Unfortunately, it’s basically guesswork. The best you can hope for is the city the IP address is being used in. If you search five different geolocation websites, you are likely to get three different answers. The only way to know for sure is to collect the data from the ISP.
Advanced IP Address Concepts
Most online investigations are fairly straightforward when it comes to IP addresses, but there are four more concepts that can throw new investigators for a loop: truncation, dynamic and static Ips, natting and VPNs.
Truncated IPv6 Addresses
IPv4 addresses are standardized and easy to recognize. IPv6 addresses, being longer, can be simplified using a method called truncation. This method significantly shortens IPv6 addresses by removing leading zeros and series of four zeros. Despite their differences in appearance, both full and truncated IPv6 addresses lead to the same destination. In the example below I changed the leading zeros color to orange. When IPv6 2001:0db8:0000:1234:0000:0567:0008:0001 is truncated, it becomes 2001:db8:0:1234:0:567:8:1 or2001:db8::1234::567:8:1
Static vs. Dynamic IP Addresses
You may have heard the term Static IP or Dynamic IP. The most common is a dynamic IP address which means the end user’s IP address may change each time as they use the internet. This allows the ISP to have more than one customer utilize the IP address. Think of it like a rental car; Avis purchases a car for their fleet and rents it to only one customer at a time. After the customer has finished their trip, the car is issued to a different driver.
The frequency in which this address changes is generally controlled by the Internet Service Provider and not the user. The end user will usually not know when their IP address has changed and may have the same IP address for a long time.
A static IP address assigns a specific IP address that remains constant. Static IP addresses are traditionally used commercially and are expensive, making them rarely seen in residential accounts. Websites and other internet infrastructure may pay for static IP addresses so they can ensure computer systems know how to communicate with each other.
IP Address Natting
Each public IP is designed to be unique and generally, IP addresses are assigned to one subscriber at a time. However, there can be situations where more than one user has the same address at the same time through a process called Network Address Translation or “Natting”.
Imagine you have a home network with multiple devices—computers, smartphones, tablets—all needing internet access. However, your Internet Service Provider (ISP) only gives you a single public IP address. NAT (Network Address Translation) solves this by assigning each device a unique private IP address within your home network. When these devices connect to the internet, NAT translates their private IP addresses to your single public IP address, making it appear as if all your devices share one IP.
Providers like AT&T Mobile use natting and Source Port numbers to enable dozens of their customers to utilize the same IP address at the same time. An example of an IP address with a source port is 44.240.245.25:32753. In this example 44.240.245.25 is the IP address and 32753 is the source port. By assigning a source port to an individual user, the ISP has created a private address to uniquely identify each customer.
NOTE: If the IP address you are investigating has a source port listed, it is always a good idea to include that in your search warrant. Without the source port the ISP likely cannot identify the correct customer.
Virtual Private Networks
To make things even more complicated, there are services that allow individuals obscure the IP address called Virtual Private Networks (“VPNs”). VPNs allow individuals to make it look like they are connecting to the internet from anywhere in the world by using the VPN’s IP address instead of their own. Imagine passing a note in class. If the person sitting next to you is the intended recipient of the note, they will definitely know that you sent it to them. A VPN works by adding another person in that scenario; you hand the note to the other student who hands it to the intended recipient. The recipient would only know who handed them the note, not who originally sent it.
This definitely throws a wrench into cybercrime investigations. Just because a VPN was used doesn’t mean your case is at the end of its road; the VPN adds an extra step in the investigative process. If you are lucky enough to encounter a VPN that keeps logs and is based in the US, the VPN provider can identify the suspects IP address which can be searched with a WHOIS lookup. It is also important to investigate every IP address used by the suspect. A VPN is a service and usually consists of an app that needs to be turned on. If the suspect slips up and forgets to turn it back on, they may accidentally log in to the thing you are investigating with their true IP address.
Writing IP Address Search Warrants
Writing a search warrant to an Internet Service Provider for an IP address is straightforward. Each ISP will have basic subscriber information consisting of the customer’s name, their phone number, billing address, service address, provided email address, and stored payment information. Some providers may maintain their user’s IP address logs which will show what addresses were assigned to the customer and may identify the websites that they visit. Additionally, some offer services like hosted email which could be collected if appropriate to your investigation.
To correctly identify your IP address in a search warrant, the IP address must include: Date, Time and Time Zone. Most ISPs simply will not comply with a warrant that does not list Date, Time and Time zone, and for good reason. It is possible that the IP has been reassigned shortly after being used by the suspect. If your warrant doesn’t specify the time zone, the ISP may default to Coordinated Universal Time (UTC) which could be hours ahead of where you are located.
Search Warrant Returns
ISPs that service residential and commercial customers often organize their return documents by service address and billing address. For residential customers, both service and billing are usually the same, but it is possible to for them to be different. For example, a parent may be paying the bill for a child in college or a PO Box might be the billing address for a business with multiple offices; the billing address is simply where the bill is being sent. The service address is where the internet connection and hardware is being used.
IP Address does not equal a suspect
It is critical to remember that just because an IP address identifies an address where it was used, it does not mean that the subscriber is the suspect. Subscriber information is an investigative lead; it only points to a digital crime scene. Investigators must conduct a thorough investigation to place the suspect behind the keyboard.
Want to write IP address warrants the easy way? Sign up for WarrantBuilder.com to get started with a free trial. Warrant Builder supports dozens of Internet Service Providers and saves you hours writing online investigation warrants. Join us for future posts in the Warrant Builder Cybercrime Field Guide series.
