In our previous blog post of the “Understanding Search Warrants” series, financial search warrants we learned there was more than one way to get the evidence we need. Today we tackle a little used technique; search protocols.
A search warrant is a fairly basic document. At its core, a search warrant authorizes law enforcement to go to a place and collect a thing. But criminal investigations are much more nuanced and sometimes require a better explanation of the steps necessary to collect the requested evidence without violating a person’s Fourth Amendment rights, preventing unnecessary intrusion and potential legal disputes down the line. Search protocols define what steps law enforcement will take to conduct the search and address legal concerns of the court along the way.
What is a Search Protocol?
A protocol is a detailed plan or guideline that outlines how a search should be conducted. These protocols ensure the search remains within the boundaries set by the warrant and respects the rights of those being searched. The protocol is a step by step plan that the affiant described in the affidavit. This provides a clear explanation of the actions that will be taken by the affiant to conduct the search. Interestingly, the search protocol is almost exclusively used in the affidavit and is rarely found in the search warrant itself. Courts tend not to want to specify the tactics and process of a search warrant, rather they review the affidavit to establish if there is sufficient probable cause to believe the thing to be collected is present at the place described and the likelihood that the crime occurred.
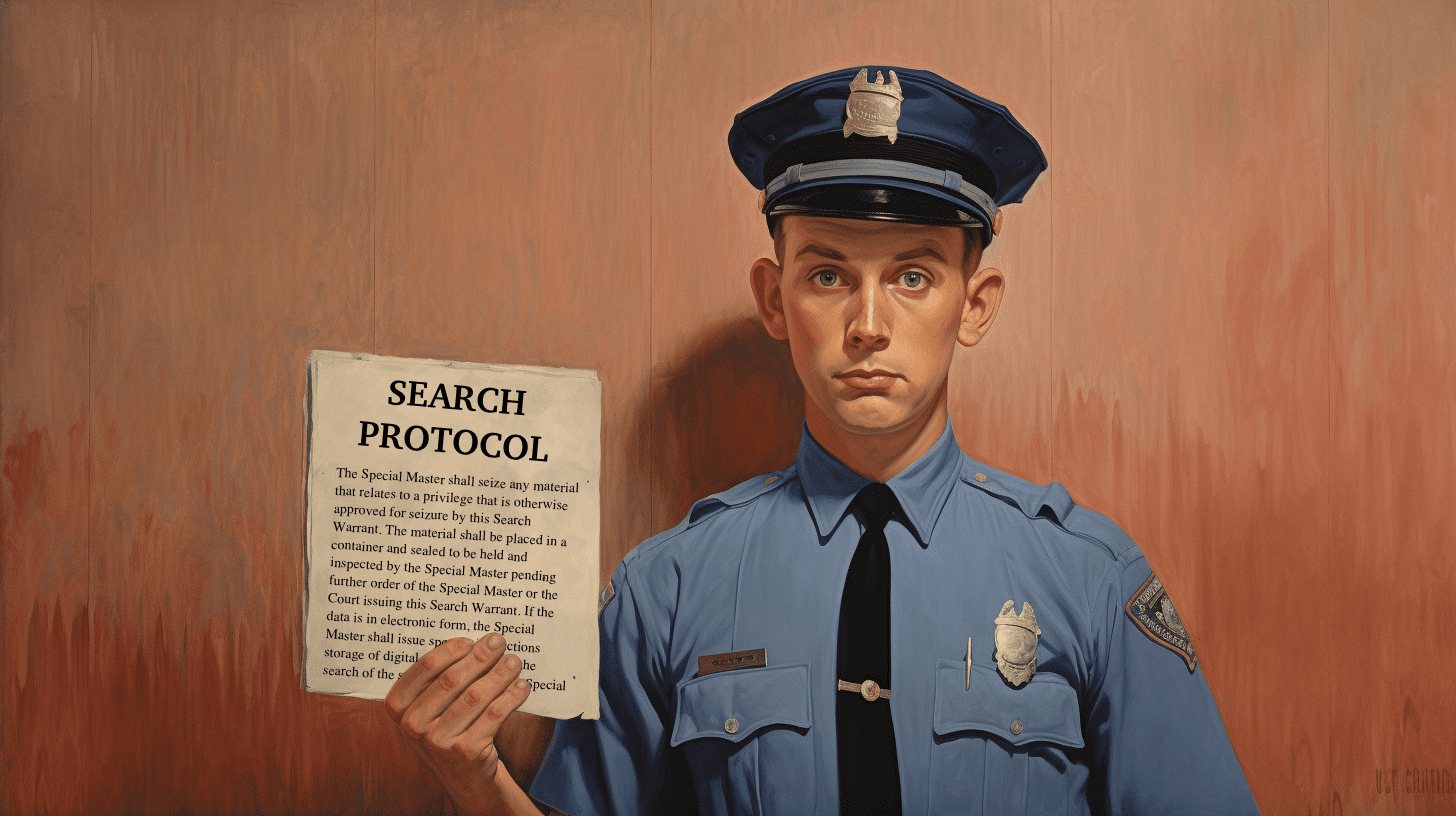
The most common example of a search protocol is the use of a Special Master. When the court issues a search warrant for documents handled by lawyers, doctors, therapists, or clergy, a Special Master might join the law enforcement agency serving the warrant. Let’s examine a common search protocol for Special Master situations: The appointment of a Special Master to conduct the search at the site listed on this Search Warrant shall be made by this Court. The Special Master shall accompany searching Peace Officers during the service of this Search Warrant. The Special Master shall seize any material that relates to a privilege that is otherwise approved for seizure by this Search Warrant. The material shall be placed in a container and sealed to be held and inspected by the Special Master pending further order of the Special Master or the Court issuing this Search Warrant. If the data is in electronic form, the Special Master shall issue specific instructions storage of digital evidence and for the search of the storage medium at the Special Master’s discretion.
Why are Search Protocols Useful?
- Clarity & Precision: Protocols provide law enforcement with clear and precise guidelines about what can be searched, where they can look, and how the search should be conducted. This prevents any confusion or overreach during the actual search.
- Protecting Rights: Protocols help ensure that individual rights are respected. An overly broad or intrusive search can be challenged in court, potentially rendering evidence inadmissible. By following a protocol, law enforcement reduces the risk of violating rights.
- Efficiency: Having a predetermined strategy can make the search process more efficient and effective, ensuring that no stone is left unturned, and that investigators don’t waste time on areas or items not covered by the warrant.
Examples of Search Protocols:
Technology-Related: Digital Device Search Protocol
Search protocols are common in digital forensic search warrants. Imagine a scenario where the police have a warrant to search a person’s laptop for evidence related to financial fraud. A digital evidence protocol in this case might include:
- Duplication: Create a forensic copy or image of the device’s hard drive to ensure the original data remains unaltered.
- Keyword Searches: Use specific predetermined keywords related to the suspected fraud (e.g., “wire transfer”, “offshore account”, names of suspected collaborators).
- File Type Restrictions: Only search specific types of files such as spreadsheets, emails, or bank transaction logs.
- Time Restrictions: Limit searches to files created or modified within a specific date range, pertinent to the suspected criminal activity.
- Third-party Access: Avoid accessing personal or irrelevant data, like family photos or unrelated personal documents.
Not every law enforcement agency has the luxury of a Digital Forensic Analyst in-house and many rely on larger allied agencies or regional labs. In these situations, the protocol often informs the Judge that the digital device, like a phone or laptop, will be transported to the lab and the forensic examination will be conducted by their personnel.
Non-Technology Related: Illegal Marijuana Grow Search Protocol
Search warrants for illegal marijuana grows often have search protocols that describe the process of documenting evidence and destruction of excess marijuana. In California, Health & Safety Code § 11479 outlines specific requirements for the bulk destruction of marijuana. Because of these requirements, California marijuana search warrants frequently contain a search protocol that informs the court the affiant’s plan for counting the total number of plants, taking weight measurements, collecting samples for evidence, and the destruction of the remaining plant material.
Anticipatory Search Warrants
One search protocol that resides in the search warrant itself is an anticipatory service protocol. An “anticipatory warrant” is a type of search warrant that is issued by a court before a law enforcement agency carries out a search. It is “anticipatory” in the sense that it authorizes a search that is expected to occur in the future, usually when certain conditions specified in the warrant are met. This type of warrant is commonly used in cases involving ongoing investigations, surveillance, or situations where the evidence sought is not immediately present but is expected to be at a specific location in the near future.
The conditions outlined in an anticipatory search warrant might involve factors such as the occurrence of a particular event or the passage of a specific amount of time. Once these conditions are met, law enforcement officers can execute the warrant and conduct the search.
For example, consider a situation where law enforcement is investigating a drug trafficking operation and has reason to believe that a package containing illegal drugs will be delivered to a specific address. An anticipatory search warrant could be obtained based on this information. The warrant might specify that the search can only be carried out if the package is actually delivered to the address. Once the package arrives, law enforcement can execute the warrant and search the premises.
Want to learn more about search warrants? Follow our blog series to learn more about how search warrants work, tips & tricks for writing great warrants, and insights on evidence that law enforcement can collect. There is a lot to learn, so rely on the experts at WarrantBuilder.com! Sign up for a free trial and learn why cops across the country trust Warrant Builder for fast, efficient, and complete search warrants.
