
The California Electronic Communications Privacy Act is a law that goes by many names: CalECPA, ECPA, and SB178. While ECPA can be a frustrating law for law enforcement to navigate, it protects the privacy of citizens while guiding law enforcement towards Judicial oversight. When writing technology search warrants in California, the ECPA is an absolute requirement; follow along to learn how CalECPA works, what makes a warrant compliant, and some exceptions to the rule.
What and why of the ECPA
In 2012, the California Electronic Communications Privacy Act (ECPA) emerged as the most comprehensive criminal privacy legislation, inspiring other states to follow suit. Senate Bill 178 introduced ECPA by amending California Penal Code Section 1546 and detailing the process for obtaining electronic evidence access. PC 1546 highlights exceptions for warrantless searches, including consent searches and emergency searches, for phones and online accounts.
Prior to ECPA, obtaining a search warrant for online records, such as a Facebook account, was tantamount to a sneak-and-peek warrant. In this scenario, an officer would gather an individual’s online data without ever notifying them of the search warrant. The rationale was that the warrant was addressed to Facebook, the data collector, which then supplied the information to law enforcement. The ECPA acknowledged that even though Meta Platforms Inc. (Facebook) acted as a custodian, the content – including photos, messages, and activities – belonged to the account owner. Consequently, if a search warrant targeted Facebook, the ECPA mandated that the account owner be informed of their data being handed over.
The 4th Amendment ensures the right of the people to be secure in their persons, houses, papers, and effects. The “papers” of 1787 are the text messages of 2022.
When does CalECPA apply?
Even after six years of being effect, officers still struggle with questions of when ECPA applies. There are three primary categories of digital evidence that are covered in ECPA. As s general guideline, ECPA covers communication, data stored within electronic devices, and a person’s location. Let’s explore some of the major key terms listed in PC §1546.
Electronic Communication Information: Any data about the person’s use of an electronic communication service, including the contents, participants, location, and identifiers of the individual or device used.
Electronic Device Information: Any data stored on or generated through the operation of an electronic device, including the current and prior locations of the device.
Understanding ECPA comes down to understanding these definitions. Electronic Communication Information covers those third party service providers like social media platforms, telecoms, messaging apps, dating sites, and pretty much anything else that resides on the internet. Electronic Device Information covers data stored inside a computer, mobile device, or electronic storage media. This includes the data encoded on the magnetic stripe of gift cards or hotel keys.
Because our phones and social media contain so much of our private lives, extra protection is afforded to these devices. As a general rule, if by looking at the data you would learn a person’s hopes, dreams, fears, what they had for lunch or where they ate it then ECPA applies.
Collecting Information
The rules for Communication Information and Device Information are different with some important distinctions. PC §1546.1(b) outlines the rules for Communication Information and §1546.1(c) outlines Device Information.
PC §1546.1(b) A government entity may compel the production of or access to electronic communication information from a service provider, or compel the production of or access to electronic device information from any person or entity other than the authorized possessor of the device only under the following circumstances: Pursuant to a search warrant, a wiretap order, an order for electronic reader records. (Civil Code §1798.90), a non-criminal subpoena, & Pursuant to an order for a pen register or trap and trace device.
You may have noticed that consent isn’t mentioned. If a person’s Instagram information belongs to them, they why can’t they consent for law enforcement to have access? Publicly available data can definitely be collected, and “Download my Data” features can be provided on consent, so why can’t the account owner consent to Instagram providing search warrant level records? Search warrant level records include Meta Platforms Inc. business records, which the account owner cannot provide consent for.
PC §1546.1(c) states that a government entity may access electronic device information by means of physical interaction or electronic communication with the device only as follows… and outlines 12 scenarios. The 12 scenarios are broken into four categories: Judicial Authorization, Custodial Situations, Consent, & Emergencies.
Judicial Authorizations
Judicial Authorizations are search warrants, wiretap orders, tracking device warrants, and pen register / trap and trace warrants. ECPA leans heavily on search warrants as the preferred remedy for collecting digital evidence. Judicial review and authorization is the extra step that safeguards some of the most private aspects of citizen’s lives.
Custodial Situations
Custodial Situations cover inmates, jail and prison facilities, parolees, probationers and pretrial release. This makes sense, inmates shouldn’t have cellphones. Probationers and pretrial release can be a bit more complicated as they require the search to be a clear and unambiguous condition of their agreement.
Specific Consent, the can of worms…
Consent scenarios are less straight forward and require the specific consent of the authorized possessor. If a device has been reported as lost or stolen, then the owner consents to a minimal search of the device that ensures the found phone belongs to them. Responding to an emergency 911 call from that device is implied consent because the caller is contacting the police to ask for help.
So there you are working your beat, trying to avoid paper before your shift ends in 45 minutes. You get dispatched to a parent reporting their 14-year-old daughter has sent some spicy pictures to a friend on Snapchat. You arrive and ask the girl for consent to search her phone to determine who the photos were sent to; she tells you to pound sand. Now what do you do?
In this scenario, the daughter is clearly the authorized possessor of the phone. Her parents are presumably the owners of the phone and let her use it. This scenario raises many questions that are not easily answered:
- Can the parent consent to the search?
- Can a parent revoke her possession of the phone, transferring it’s “authorized possession” to themselves?
- Does ownership of the device imply ownership of the data therein?
There are no easy answers here and there isn’t any clarifying case law. Going through the phone of a 14-year-old girl is akin to reading her diary, and it seems prudent that the Court would want to extend the protections of privacy even to a minor that is at the heart of this law. In short, get a warrant.
Emergency Search & Disclosure
If there is an emergency involving danger of death or serious physical injury to any person requires access to the device information, law enforcement can access both Communication Information and Device Information. PC §1546.1(h) requires that an Officer must apply for a search warrant within three days of the emergency search.
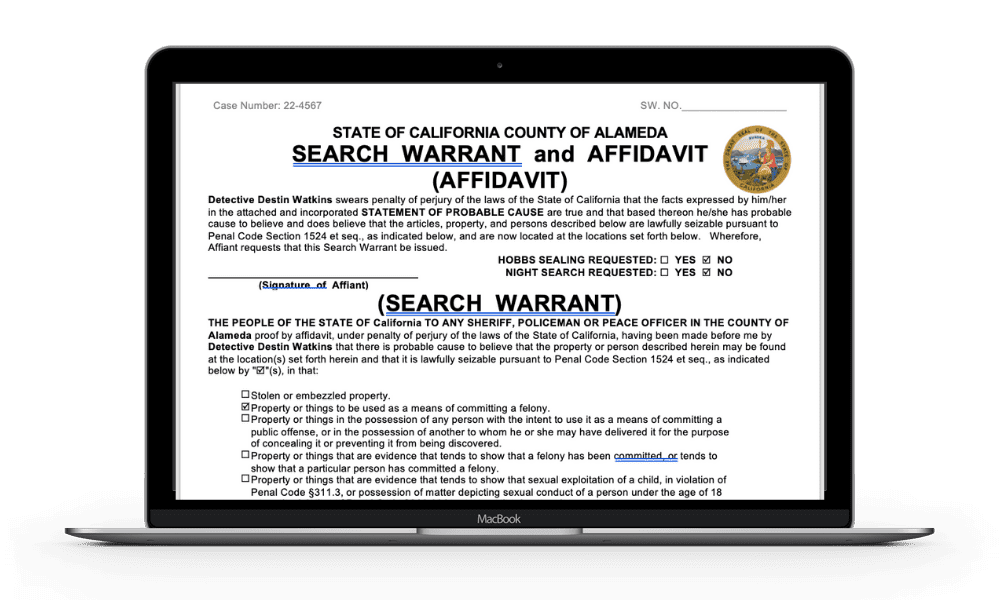
ECPA Compliant Search Warrants
All roads lead to Rome. With the California ECPA, all roads lead to a search warrant. Penal Code §1546.1(d) explains what a search warrant needs to be compliant. If relying on a search warrant template, officers should double check that all the requirements are covered.
For both Communication and Device Information, ECPA requires that the warrant specify the start date and end date for the records officers seek to collect. It is best to specify the date, the time and the timezone. eg. 8/26/2022 at 08:00:00 UTC to 8/27/2022 at 17:05:23 UTC. If the timezone isn’t specified, the Electronic Service Provider may make a decision to provide records in Universal Time Code instead of your timezone. This can cause your evidence to be outside the requested window. PC §1546.1 allows for situations where a beginning and end cannot be specified. The officer needs to provide an explanation as to why it isn’t feasible. For example, the online file storage service Dropbox cannot provide files between two dates. Dropbox can provide everything or nothing. The officer should request everything and outline a review protocol that could narrow down files to a specified time frame.
CalECPA also requires an a Court Order that seals any data outside the specified time frame. This prevents the overcorrection of information that is not directly connected to the investigation. For example, if a suspect is selling fentanyl on WhatsApp and a search warrant collects unrelated messages between the suspect and his grandmother about her upcoming 90th birthday, those messages must be separated and sealed. How and when those are sealed are questions to talk with your DA or agency attorney about.
Finally, when electronic communication information is involved, an Authenticity of Record Court Order is required. This simple order tells the Electronic Service Provider to send a letter with the return that states the provided records are true and correct.
Clear as mud…
The California Electronic Communications Privacy Act was written by a group of people who don’t know how to change the time on their VCR, but I believe that their heart was in the right place. When you think of how much of your personal life exists within your phone, I think you will agree that it should have some special protections from prying eyes. The search warrant requirement does add an extra step, but it is important to remember that the extra step is Judicial review.
Want to write California ECPA compliant search warrants? Sign up for a free trial of Warrant Builder
